Blog
Cybersecurity Journey: Building a Secure Enclave to Protect CUI

Get ready to take charge of your Cybersecurity Maturity Model Certification (CMMC) compliance journey by establishing a strong foundation for success in the evolving landscape of defense contracting. As you navigate the path to CMMC compliance, one of the crucial initial steps involves determining the scope of the systems responsible for handling controlled unclassified information (CUI). This process often leaves organizations searching for clarity to define what’s within the boundaries for evaluation and what falls outside.
In a recent Exostar webinar with trusted partner RSM US LLP, we cover the essential skills required to confidently answer this critical question and properly scope and build your CUI secure enclave. Watch the recording for valuable insights and practical strategies to address compliance issues and boost your compliance efforts.
This webinar can help elevate your organization’s cybersecurity posture and tackle NIST 800-171/CMMC compliance issues. Topics covered include:
- Identifying your boundary: Understand compliance scope, manage data flow efficiently, and gain practical techniques to achieve compliance
- Building your secure enclave: Strengthen security with architectural principles, technical controls, and alignment with CMMC/NIST 800-171
- Enclave security design costs and considerations: Make informed design choices, optimize compliance, and streamline the process with expert insights on security and cost drivers and solutions.
With 2024 on the horizon and CMMC’s imminent arrival, be prepared to meet compliance standards and thrive in the ever-evolving cybersecurity and compliance landscape. The consequences of non-compliance can be detrimental, causing financial strain, operational complexities, and increased security vulnerabilities.
Understand your relationship with CUI and its impacts on your business
External factors:
- Your Customers — agencies you work with
- Your Partners — your primes and subs as well as their requirements to work together
- Your Contracts — clauses that are already in your contracts
- Your Future — where your business will be in 2-3 years
Internal factors
- Your Data
- Do you have CUI?
- Do you have export-controlled data?
- Can you segment it from the rest of the organization?
- Your People
- Who directly interacts with CUI? Who indirectly interacts with CUI?
- Which systems store, process, or transmit data?
- Your Sources
- Where do you get CUI or send it inside and outside of your organization?
To better understand CUI, consider the following categories and examples:
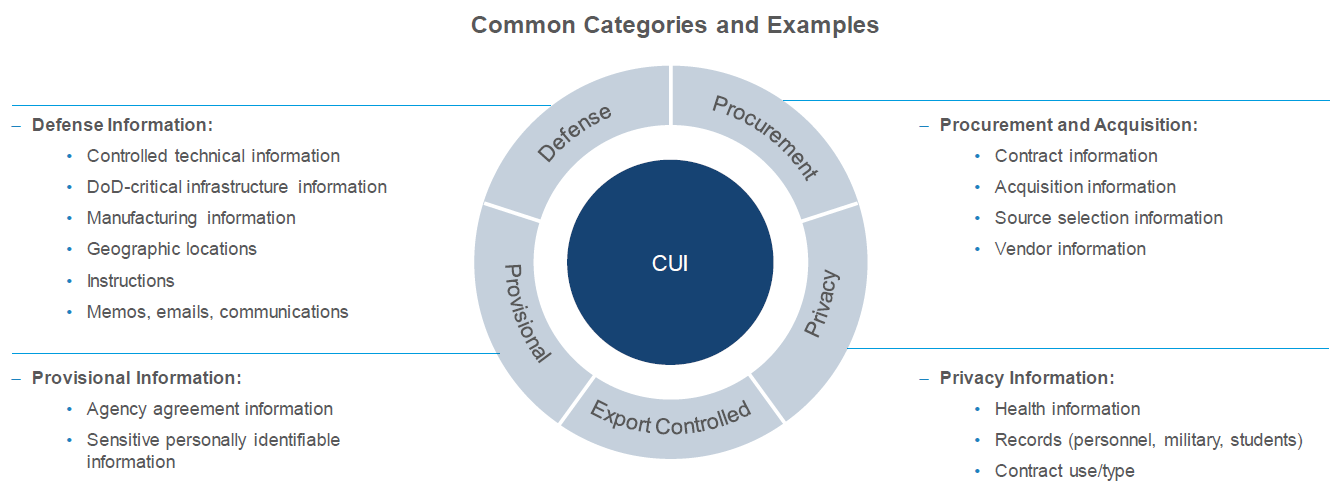
CUI data flow diagrams demonstrate that the organization has a comprehensive understanding of the interconnected business processes handling CUI. This helps ensure that associated business processes are not missed and provides insight on where to apply applicable, mandated regulatory controls.
Drivers of your strategy include the level of knowledge of the business and the data, technical debt, documentation, any previous investments, resources, expertise, and availability.
Costs can be direct or indirect, such as internal resources and consultants, or indirect, such as organizational impact beyond IT and business process changes.
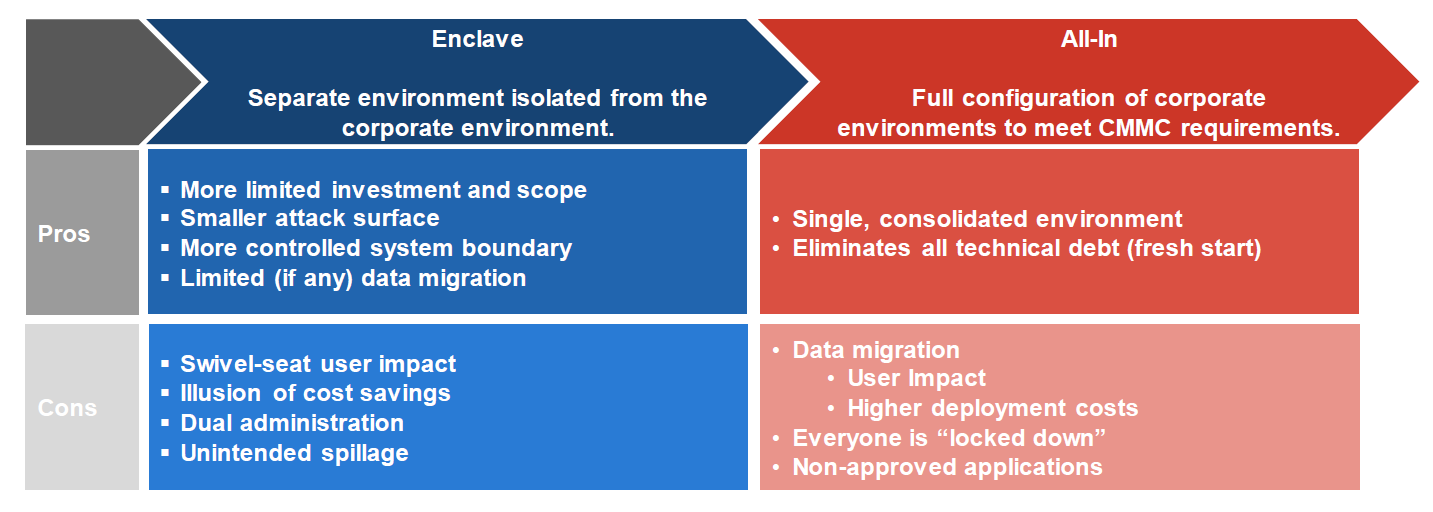
Understanding Options: Secure Enclave vs All-In
The table below compares pros and cons of the Secure Enclave option — a separate environment isolated from the corporate environment — versus the All-In option — a full configuration of corporate environments to meet CMMC requirements. Turning to an MSP-based solution (like Exostar’s Managed Microsoft 365) can help mitigate potential cons of the secure enclave approach.
Building out a secure enclave and how to best protect data
In the webinar recording, we go through the details of a secure enclave build-out, including the following steps:
- Discover — CMMC Readiness Assessment
- Design — POAM and SSP development
- Deploy — Training and organizing team members
- Optimize — Joint surveillance
You’ll also learn about protecting data, such as sensitivity labels that act as stamps for corporate documents and files that lets you classify and protect your organization’s data, while making sure that user productivity and their ability to collaborate isn’t hindered.
The discussion explores the sea of vendors involved at each point, to take care of Identity and Threat Protection, Device & Apps Management, and Information Protection and Governance.
Last but not least, discover how everything fits together with Microsoft tools that you are already using.
For detailed insights from the experts at RSM and Exostar, we invite you to watch the recording.
You are welcome to schedule a conversation with a cybersecurity expert at Exostar for information about the best solutions for your organization.