Blog
CMMC POAMs: Guidelines and Limitations

Whether you are learning about Cybersecurity Maturity Model Certification (CMMC) or already started a System Security Plan (SSP) and self-assessment, you may be concerned that your organization does not currently meet all the required 110 National Institute of Standards and Technology Special Publication (NIST SP) 800-171 controls.
While a Plan of Action and Milestones (POA&M or POAM) can help bridge the gap in the interim, there are some caveats worth keeping in mind. In this post, we’ll outline how a CMMC POAM fits into the other steps you must take on the journey to a CMMC-compliant status and share POA&M limitations and guidelines.
If you are unfamiliar with many of the preceding acronyms, then please read these two posts that share an overview of CMMC and NIST SP 800-171. Although POA&Ms may buy some limited time while working toward full CMMC 2.0 compliance, you still must create an SSP and satisfy the majority of the NIST SP 800-171 controls before beginning the formal certification process, which benefits from a foundational understanding of CMMC/NIST.
What Is a POAM?
A POA&M is a document that identifies tasks an organization must accomplish to resolve security weaknesses. This document details the resources required to accomplish elements of the plan, any milestones for meeting the tasks, and scheduled completion dates, among other information.
Previously, the Department of Defense (DoD) did not allow organizations to use a Plan of Action and Milestones during the CMMC compliance process. However, under CMMC 2.0, contractors meeting most of the controls laid out by NIST SP 800-171 can use time-limited POA&Ms to maintain contracts and, upon resolving those POA&Ms, achieve full CMMC compliance at level 2 or level 3. This contingency plan ensures organizations have time to implement CMMC 2.0 requirements and correct cybersecurity vulnerabilities without losing valuable contracts.
How POA&Ms Fit Into the CMMC Assessment Process
First, determine which CMMC 2.0 maturity level applies to your organization. The DoD only allows POA&Ms for CMMC levels 2 and 3.
Then, your organization will begin preparing for CMMC assessment by evaluating your cybersecurity infrastructure against CMMC requirements. Understanding the 110 NIST SP 800-171 controls is essential for performing a cybersecurity gap analysis and developing an SSP.
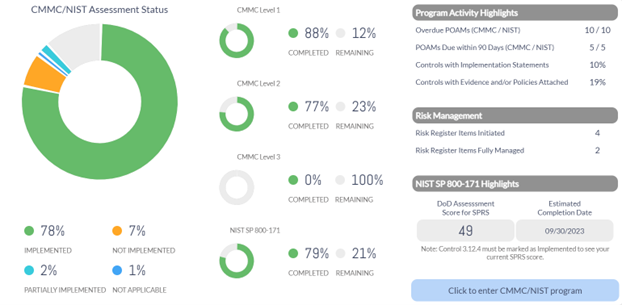
When you complete a basic self-assessment against the 110 NIST SP 800-171 controls, your score will range from -203 to 110, and you will report your score to the Supplier Performance Risk System (SPRS).
CMMC POAM Requirements and Limitations
Beginning the formal CMMC assessment process with a CMMC Third-Party Assessor Organization (C3PAO) requires a SPRS score of at least 88. Each NIST SP 800-171 control is worth 1, 3, or 5 points, and POA&Ms are only allowed for 1-point controls, excluding the following 1-point CMMC CUI controls for CMMC level 2:
- AC.L2-3.1.20 – External Connections (CUI Data)
-
- Verify and control/limit connection to and use of external systems.
- AC.L2-3.1.22 – Control Public Information (CUI Data)
-
- Control CUI posted or processed on publicly accessible systems.
- PE.L2-3.10.3 – Escort Visitors (CUI Data)
-
- Escort visitors and monitor visitor activity.
- PE.L2-3.10.4 – Physical Access Logs (CUI Data)
-
- Maintain audit logs of physical access.
- PE.L2-3.10.5 – Manage Physical Access (CUI Data)
-
- Control and manage physical access devices.
One 5-point control may also permit a POA&M, SC.L2-3.13.11, if it is partially met—encryption is employed but is not Federal Information Processing Standard (FIPS) validated—reducing a SPRS score by 3 points instead of 5.
For your reference, we sourced these POA&M guidelines from the CMMC Proposed Rule by the DoD: Section 170.21 on POA&Ms. View additional POA&M control exemptions for CMMC maturity level 3 in the linked section. POA&Ms are not permitted for CMMC maturity level 1 controls.
Key Information in a POA&M
Each POA&M you open must contain the following information necessary for review and approval by a third-party assessor or for a self-assessment submission:
- The relevant control
- The responsible party
- Planned actions to meet the control
- Start and completion dates
- Milestones to meet and interim completion dates
- The actual actions taken
- Status (ongoing or complete)
Closing Out a POA&M
Your organization must resolve identified vulnerabilities and close out the POA&M within 180 days (six months) of achieving a Conditional Certification Assessment.
If the POA&M was created during an annual self-assessment, your organization will perform the closeout assessment. If it was identified by a C3PAO or certified CMMC assessor during a triennial assessment, the third party will perform the closeout assessment, which may require an additional on-site visit.
Streamline Your Compliance Journey Today
Complying with DoD standards can be a complex and time-consuming process. Exostar’s Certification Assistant is a cloud-based tool designed to streamline the CMMC self-assessment process in alignment with NIST SP 800-171 and CMMC. Simplify your CMMC compliance journey with a secure tool where you can:
- Complete your self-assessment
- Calculate your SPRS score
- Generate your SSP with one click
- Securely store and handle documentation
If your organization needs to create POA&Ms, Certification Assistant provides a user-friendly interface in which you can manage and track the entire process, including setting a due date, showing open POA&Ms, assigning them to responsible internal or external parties, displaying action items, and notifying parties of overdue tasks.
Certification Assistant enables your organization to gather all necessary documentation for outside assessors in one secure space to readily satisfy third-party assessments.
Purchase Certification Assistant or request your free trial today.* Exostar endeavors to make CMMC compliance simple and affordable for prime and subcontractors—please connect with an expert to learn more.
*Free trial available to existing Exostar Managed Access Gateway (MAG) users only. Fill out the form on this page to request access.